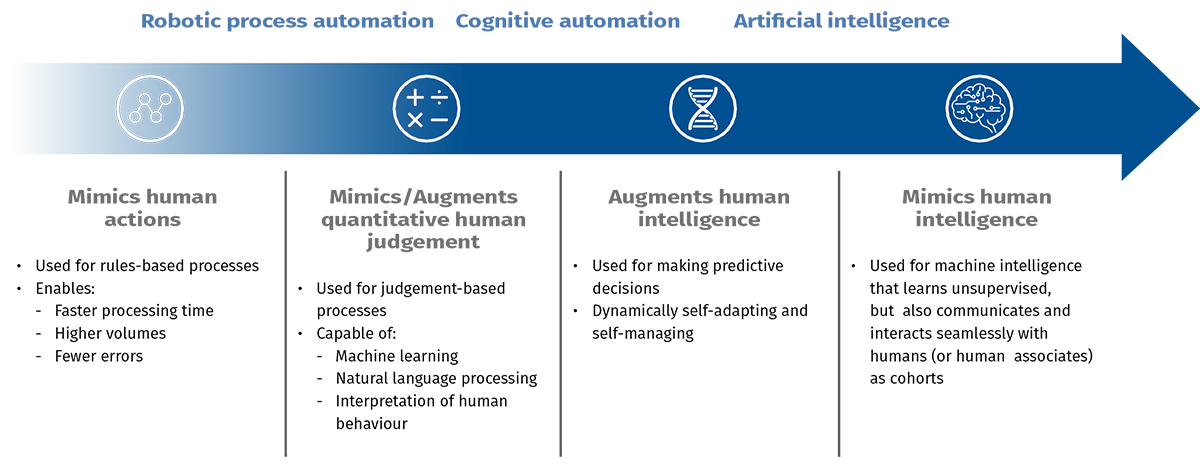
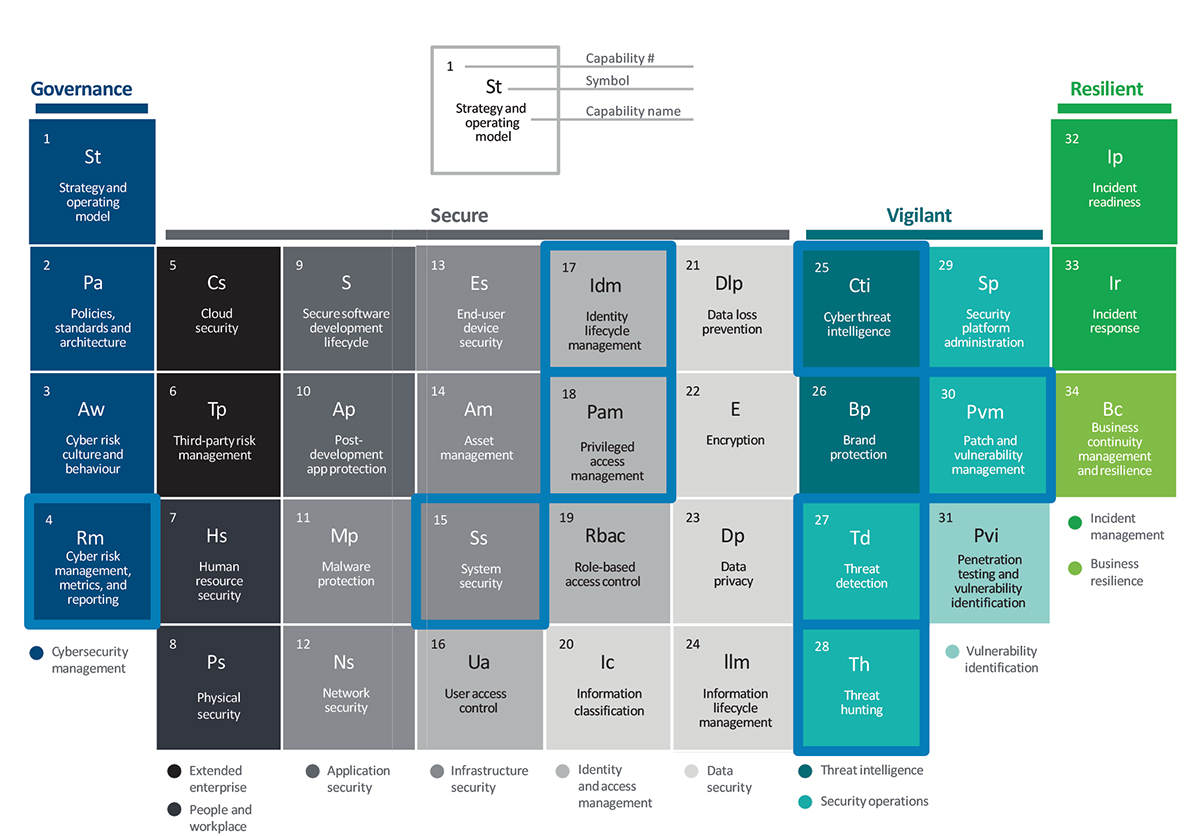
The following are some potential uses for automation in specific cybersecurity areas under the different pillars, which may include multiple elements in the table.
Element 4: Cyber risk management, metrics, and reporting
Governance and risk management
Informs overall strategy and improves reporting capabilities by using large volumes of contextual data and decision points to help with strategic decision making that aligns with the organisation’s risk appetite.
Regulation synthesis and mapping
Develops and maintains an organisation’s integrated security controls framework, extracting information from multiple regulatory sources and guidelines.
Assessment triggering
Conducts automated assessments periodically, or is triggered automatically by changes to applications and/or business processes.
KRI automation
Automates the collection and visualisation of key risk indicator metrics to enable the organisation to assess and address risk exposure.
Responsibility allocation
Uses self-service processes to allocate cybersecurity responsibilities across teams, improving efficiency and enabling closer alignment with risk owners.
Control testing
Automates control testing so that it continually assesses control effectiveness and provides near-real time updates about the organisation’s security posture.
Elements 17 and 18: Identify lifecycle management; Privileged access management
Role maintenance
Uses an AI engine to provide recommendations on role maintenance, helping organisations streamline the difficult, costly, and time-consuming task of keeping role definitions up to date.
Role mining engine
Extends the role maintenance engine to mine roles from multiple data sources, recommending new roles and entitlements.
Access request recommendation engine
Makes the access request process simpler by analysing various data sources – such as peer group access and historical access requests – and then recommending the level of access required for a user.
Access certification analytics
Analyses different data sets and applies analytics to improve the certification process by pre-approving certification items based on access request data, detecting anomalies in the attestation cycle, and using peer group data to calculate a confidence score that helps reviewers make informed decisions.
Access usage data for analytics engine
Incorporates access usage data into the analytics engine to help it generate more informed and efficient insights.
At the more sophisticated end of the technology spectrum, the following are some of the many potential uses for AI and analytics technologies in cybersecurity.
Element 15: System security
Control effectiveness
Augments and assesses the effectiveness of tried and tested tools such as firewalls, proxies, and data loss prevention solutions by monitoring the available log data and then identifying and remediating misconfigurations.
Element 27: Threat detection
Anomalous behaviour detection
Helps identify anomalous data access activity and malicious application activity by focusing on user logins, changes in user behaviour, and unapproved changes.
Threat discovery
Monitors activities and entities to establish normal behaviour, and detects sources of anomalies that could create potential risks such as fraud, money laundering, and insider threats.
Alert cleansing and prioritisation
Uses machine learning to significantly automate the first level of triage based on factors such as type of attack, frequency, and previous experience.
Targeted investigation and support
Uses a big data platform to drive new insights through historical analysis, thereby allowing investigations into incidents based on current and historical data to be done quickly and efficiently.
Element 25: Cyber threat intelligence
Cyber risk sensing
Identifies or predicts risks that are often difficult for humans and rules-based systems to detect, including new categories of risks, diffused risk signals, and potential sources of future risks such as increased use of social media.
Elements 28 and 30: Threat hunting and vulnerability management
Threat hunting
Quickly searches for new threats by importing known tactics, techniques, procedures, and attack patterns – along with vulnerability details and remediation information – to help neutralise threats early in the attack cycle.
Vulnerability scanning
Uses bots to initiate and scan applications, systems, and other assets for vulnerabilities, assessing risk and prioritising the patch schedule.
Configuration review
Uses bots to review system configurations to ensure baseline hardening and ensure no misconfigurations.
Attack path modelling
Performs predictive analytics on security data to determine vulnerable entry points and the likely path an attacker might use to gain access.
FROM FRAMEWORK TO PRACTICE
There are seven steps you can start taking today to boost your organisation’s cyber capabilities through the use of AI technologies and analytics.
Step 1 Embrace the future
Collaborate with your ecosystem to help shape the future of these powerful new cyber technologies.
Step 2 Educate yourself and your teams
Understand the business opportunities associated with AI technologies and analytics in cyber, immersing yourself in internal forums and decision-making processes to ensure you are a valuable contributor.
Step 3 Reassess the risk and threat landscape
Understand the impact of new technologies and develop appropriate risk management responses.
Step 4 Redefine your accountability model
Consider how changes in the operating environment will affect the risk landscape and required controls, and then adjust your cyber team’s roles and responsibilities accordingly.
Step 5 Rationalise your control framework
Encourage risk-intelligent design for new systems, technologies, and control frameworks to reduce unnecessary control layers and build more preventative and automated capabilities upfront.
Step 6 Start small and scale fast
Develop a practical strategy for applying AI technologies and analytics to cybersecurity by identifying opportunities with high impact, low complexity, readily available data, and insufficient current capabilities.
Step 7 Rethink your cyber talent strategy
Update your talent strategy, taking steps to ensure highly skilled cyber professionals are leading the way in your cybersecurity efforts.
AI technologies and analytics can lift your company’s cyber capabilities to the next level. By taking the lead on applying these disruptive innovations to cybersecurity, you can tip the balance in your favour and stay a step ahead of the threats.
Nick Galletto is Global and Canadian Cyber Risk Services Leader, Deloitte.
This article was originally published in the ISCA Journal.